Fixed Zero-day vulnaribility in Sign in with Apple
Developer and security researcher Bhavuk Jain reported a serious security flaw in the “Sign in with Apple” login service and received a $ 100,000 award from Apple. At the same time, Apple has been able to fix the error.
Now, the details of the recently fixed zero-day vulnerability in the “Sign in with Apple” login have been published. The vulnerability allows an attacker to control the user’s account. Since “Logging in with Apple” is associated with an Apple ID. This can have disastrous consequences for Apple users.
The vulnerability discoverer, Bhavuk Jain. He has now explained this in a blog post. Jain had shared his findings with Apple in April. Now that the vulnerability has been closed. He has made all information public.
The procedure has now been changed
The new authentication method “Login to Apple” has been presented as a more privacy-friendly alternative to website and app login systems, as no further personal data has to be transferred. And started with iOS 13 last autumn. Apps and services that offer login options with Facebook or Google accounts can use the Apple alternative on iPhone or Mac.
Jain explained the problem. Logging in to Apple works either with a JSON Web Token (JWT) or with a code generated by Apple’s servers, the latter being used to generate a JWT if it does not exist. Apple creates a JWT to log in that contains the user’s email ID and is used by the third-party application to log in to the user.
Jain discovered that it is possible to request a JWT for any email ID. Once the token’s signature is verified with Apple’s public key, it is considered valid. In fact, an attacker could use this procedure to create a token and gain access to the victim’s account. Apple has therefore changed the procedure so that the vulnerability is no longer available. According to an investigation by the Apple security team. The vulnerability has so far not been used in any known attack.
Zero-day in Sign in with Apple
According to the blogger In April, I discovered that the zero-day time of logging in with Apple affected the third-party applications that were using the service. And did not implement their own other security measures. The vulnerability could cause the user account on the third-party application to be taken over by a full account, regardless of whether the victim has a valid Apple ID.
Technical Details
The Sign in with Apple works similarly to OAuth 2.0. There are two possible ways to authenticate a user by either using a JWT (JSON Web Token) or a code generated by the Apple server. The code is then used to generate a JWT. The below diagram represents how the JWT creation and validation works.
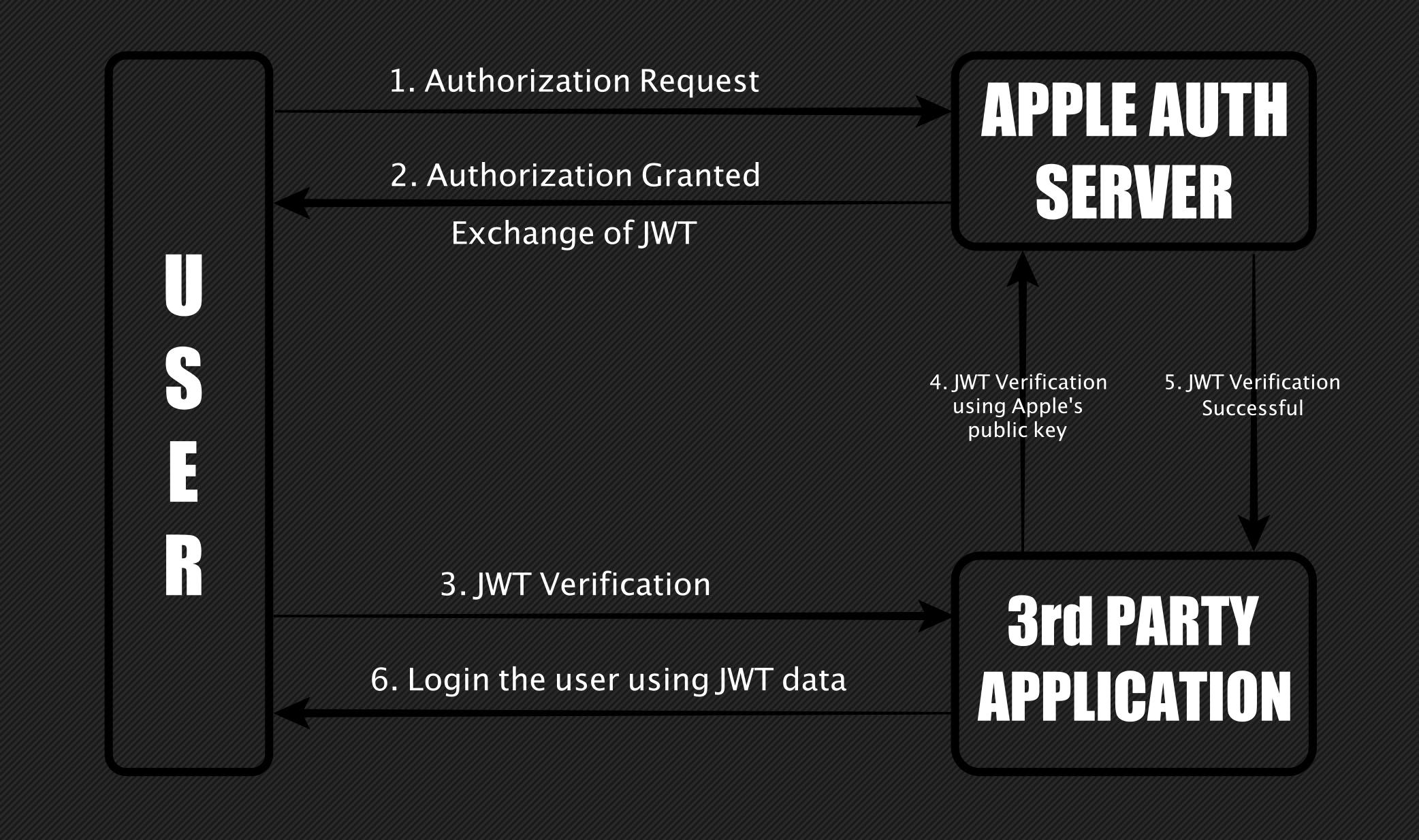
In the second step, when authorizing, Apple will provide users with an option to choose whether to share the Apple email ID with third-party applications. If the user decides to hide the email ID. Apple will generate its own user-specific Apple relay email ID. According to the user’s choice, after successful authorization, Apple will create a JWT that contains this email ID. And then the third-party application will use this ID to log in to the user.
Also Read:
These functions now come to an end after Windows 10 May Update:
What will show at the presentation of the PlayStation 5
Huawei in panic mode because of US embargo






