Android’s new banking trojan bypasses Google’s two-step authentication

Android’s new banking trojan steals PINs and pattern keys along with Google Authentic codes. Threat Fabric, a Dutch company is specializing in mobile security. The company talked about new malware that is threatening Android-based mobile devices.
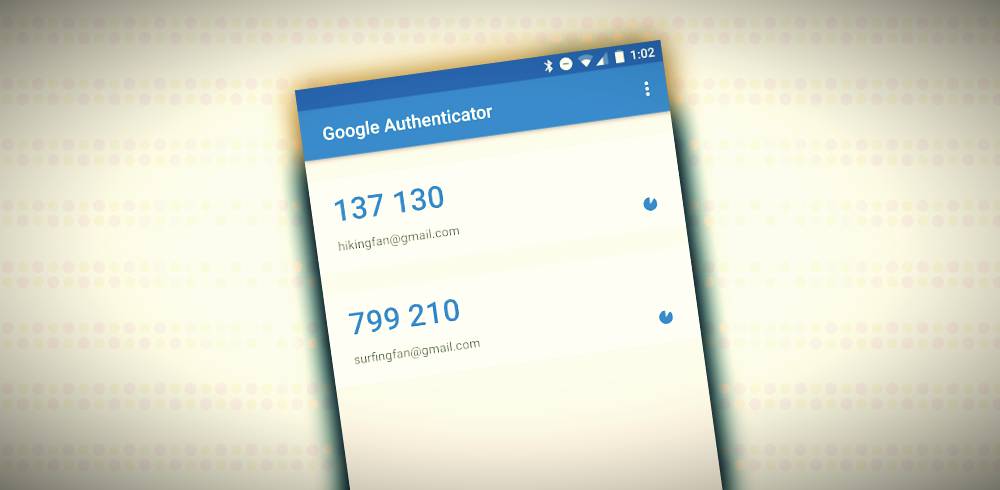
The new version of Banking Trojan Cerberus is capable of stealing one-time codes generated by the Google Authenticator two-step verification request. Cerberus also bypasses Google’s two-step authentication. While Google Authenticator application is the best known for protecting two-step verification accounts.
In Past, Google launched the Authenticator application in 2010 as an alternative to sending SMS codes. Because such codes are built on a user’s smartphone and do not transmit over unsecured networks. This method of protection considered more reliable than SMS codes.
In addition to circumventing Google Authenticator, Cerberus bypasses Google’s two-step authentication. Because there is no problem for the Trojan to bypass the PIN code or unlock pattern.
The report notes that when Google Authenticator is running. The Trojan may receive confidential content and send it to its servers.
According to experts, this type of Cerberus was apparent in January 2020 and is not yet widespread. And it is apparently in the testing phase. For such Trojan online banking services. There is a serious threat.
The Cerberus banking Trojan
In a report published this week, security researchers at Dutch mobile security company Threat Fabric reported that they had stolen an authentic OTP in a recent sample of the relatively new Android Banking Trojan. This trojan launched in June 2019.
Threat Fabric said that this new feature is not yet live on the advertised and sold Cerberus version on herring forums.
This Banking Trojan appeared at the end of June 2019. Cerberus has taken on the status of major banking malware leasing from the infamous Anubis Trojan. Cerberus Banking Trojan Offering a feature set that enables successful identification of personally identifiable information (PII) from affected devices. Cerberus still lacks the features that use stolen information and fraudulent misuse. This can be helpful in reducing the detection barrier. In mid-January 2020, after the New Year’s celebrations. Cerberus authors came up with a new format that aims to address this issue
Cerberus has been refactoring to update codebase and C2 communication protocols. But in particular to steal RAT capabilities, device screen lock credentials (PIN codes or swipe patterns) and 2FA tokens. Cerberus Has ability to bypass Google Authenticator application.
Source = Threat Fabric
Also, Read
OPPO Find X2 announces 120Hz screen details: independent chip, dynamic frame insertion!
Huawei P40 Pro revealed a weakness – ultra-fast charging disappoints fans
Zhong Nanshan: New coronavirus pneumonia epidemic does not necessarily start in China






